Secure and Go
Sharing experiences on Oracle Fusion Middleware security
Monday, June 27, 2011
Moved
I am now blogging with my team colleagues at http://fusionsecurity.blogspot.com. Lots of cool stuff. Look forward to meet you there.
Thank you.
Andre.
Tuesday, November 30, 2010
Security in Service-Enabled ADF Business Components
This article is a developer-focused tutorial where operations carried by ADF BC (Application Development Framework Business Components) are exposed as web services, so they can be easily integrated into SOA applications. I will describe the end to end development process, starting with service-enabling ADF BC Application Modules, showing how to secure them and how to package the application using JDeveloper.
Service-Enabling ADF Business Components
So let’s take a look at how service-enabling business logic encapsulated in ADF BC looks like. Roughly put, ADF BC comprise 3 main components: Entity Objects (EOs), View Objects (VOs) and Application Modules (AMs). EOs are the object representations of a business domain, VOs are the queries built on top of those objects, giving shape to data, and AMs are the way in which data and business logic is exposed to the outside world. I strongly recommend reading JDeveloper’s embedded documentation on ADF for the full picture. ADF BC is a very powerful framework and aims for quick and consistent development of java-based enterprise-wide applications. It is worth mentioning that is the natural path for the thousands of Oracle Forms customers to enter an SOA world.
AMs are the entry point for encapsulated business logic. They are the components for which web services interfaces are created. Service-enabled AMs are stateless enterprise session beans that are added a SOAP binding. One can expose any AM public custom method or any VO method as a service operation. And each of these operations can be added distinct security policies.
As an example, I am considering an SOA Loan Application. In order to make a decision whether or not the Loan should be granted to the requester, the application needs to query an AM for the requester payment history. This is precisely the AM that I will make available as a SOAP web service.
Here is the sequence:
1 – VO definition
This is a read-only VO, meaning it is not based on an EO, so you cannot update data through it. It queries a database for the customer payment history.
Couple of things to notice:
a) customerName bind variable, used in the specified view criteria.
b) CustomerPaymentHistoryVCByName view criteria, allowing any name to be added to the query at runtime.
2 – Service Enabling the AM and exposing View Criteria as a web service method
a) Double-click the AM (CustomerHistoryAM) in the Application Navigator on the left side, click Service Interface (on the right side) and then click the green plus sign on the top right.
Attention to the Target Namespace field value. That’s vital information when it comes to securing the web service. More on this later.
Also see that there’s an option of generating asynchronous web services methods. I will cover it in a future article.
Click Next button.
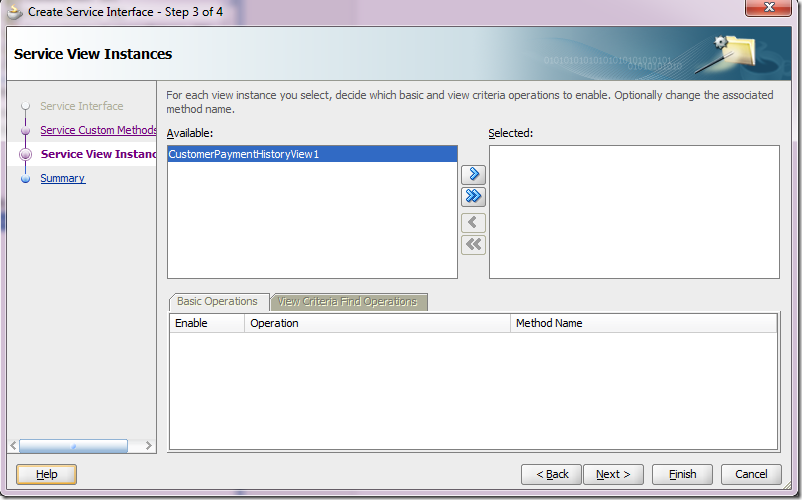
b) On the left side, click Service View Instances, pick the VO instance, select it and send it to right side using the blue arrow.
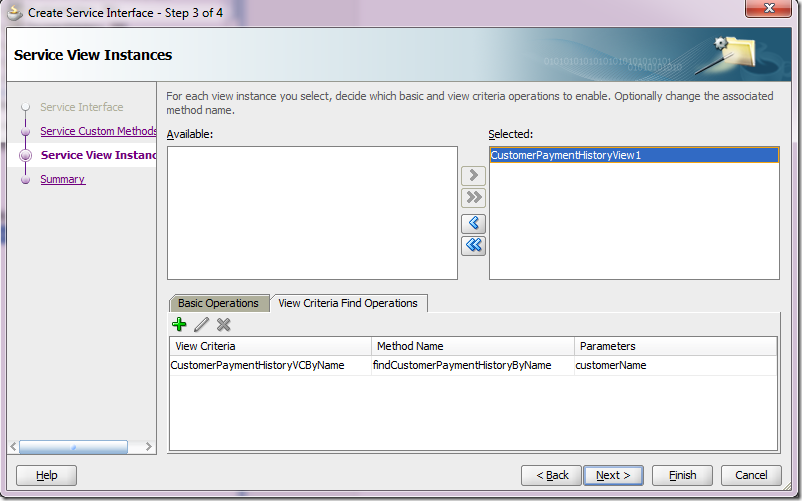
c) Select View Criteria Find Operations tab and click on the green plus sign.
d) Pick the View Criteria that was previously created in step 1 and give the operation a more meaningful name. The binding variable defined for the view criteria is automatically exposed as an input parameter.
Click Ok.
e) The View Criteria gets exposed as a method that takes the binding variable as an input parameter. Click Next.
f) In the summary screen, do notice the Service Interface name (highlighted). It will be used when securing the service.
g) Upon clicking the Finish button, here’s what we get:
Four classes are defined for the Application Module. For the purposes of security we’re interested in the Remote Server Class, which is the web service implementation.
Securing the web service
Securing the web service here means attaching an OWSM authentication and an authorization policy to it. Both are attached at the service level, meaning all operations are now protected. However, different operations can be granted to different subjects.
1 - Adding OWSM Policies to the Web Service
In this example, the authentication policy is a username-based one, which means this web service expects a username token in the incoming SOAP message header. The authorization policy delegates the authorization decision to the OPSS layer, which expects an authorization policy defined in the OPSS policy store.
a) To attach the policies, place the cursor over the web service implementation class name (CustomerHistoryAMServiceImpl.java). In the property inspector, under Web Services Extension, under OWSM Policies, click the … button next to Security
b) Pick the following policies from the list:
oracle/wss_username_token_service_policy and oracle/binding_permission_authorization_policy.
Notice they are added as a SecurityPolicy class annotation.
These policies can also be added/removed/changed in Enterprise Manager.
At this point, all operations of our web service will require a valid user, but there’s still no authorization rule governing which users can access the findCustomerPaymentHistoryByName method. Let’s take care of it now.
2 - Adding the OPSS Authorization Rule to the Web Service Operation
As you might think, these authorization rules are expressed in the OPSS policy store. At design time, this translates to creating the rule in jazn-data.xml. Let’s assume that we only want to allow members of the manager role to invoke the findCustomerPaymentHistoryByName method.
Here’s the jazn-data.xml snippet.
Attention to lines 15-31. They define the authorization rule for our method.
1: <?xml version = '1.0' encoding = 'UTF-8' standalone = 'yes'?>
2: <jazn-data xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
3: xsi:noNamespaceSchemaLocation="http://xmlns.oracle.com/oracleas/schema/jazn-data-11_0.xsd">
4: <policy-store>
5: <applications>
6: <application>
7: <name>CustomerHistory</name>
8: <app-roles>
9: <app-role>
10: <name>managers</name>
11: <class>oracle.security.jps.service.policystore.ApplicationRole</class>
12: </app-role>
13: </app-roles>
14: <jazn-policy>
15: <grant>
16: <grantee>
17: <principals>
18: <principal>
19: <name>managers</name>
20: <class>oracle.security.jps.service.policystore.ApplicationRole</class>
21: </principal>
22: </principals>
23: </grantee>
24: <permissions>
25: <permission>
26: <class>oracle.wsm.security.WSFunctionPermission</class>
27: <name>/customerhistory/common/CustomerHistoryAMService#findCustomerPaymentHistoryByName</name>
28: <actions>invoke</actions>
29: </permission>
30: </permissions>
31: </grant>
32: </jazn-policy>
33: </application>
34: </applications>
35: </policy-store>
36: </jazn-data>
Line 19 contains the role name granted the permission to invoke the method.
Line 26 defines the permission class that understands the name and actions specified in lines 27 and 28. oracle.wsm.security.WSFunctionPermission is mandatory for authorization rules based on OWSM authorization policies.
Line 27 defines the web service and the operation name being protected. Here is where we need the web service namespace and name, as said in subsection 2f above. You can also find this information in the service wsdl.
The format is <webservice-target-namespace>/<webservice-name>#<method-name>
And yes, you can use * in place of <method-name> and protect all methods in one shot.
Line 28 defines the action. The only available and allowed for webservices at the time of this writing is invoke.
Deploying the Application
To deploy an application like this, it is necessary to create a Business Components Service Interface Deployment Profile and then deploy it to an EAR file.
a) In JDev’s Application Navigator, right-click your project and select New…
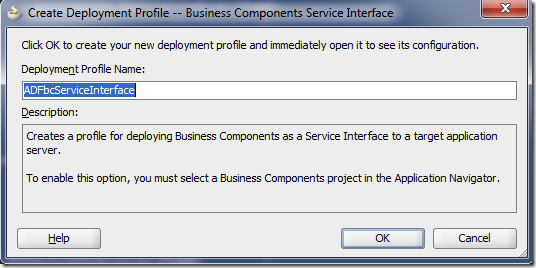
Under General Categories, choose Deployment Profile and pick Business Components Service Interface in the right side.
Upon clicking OK button, give it a meaningful name and click OK
The deployment profile gets created.
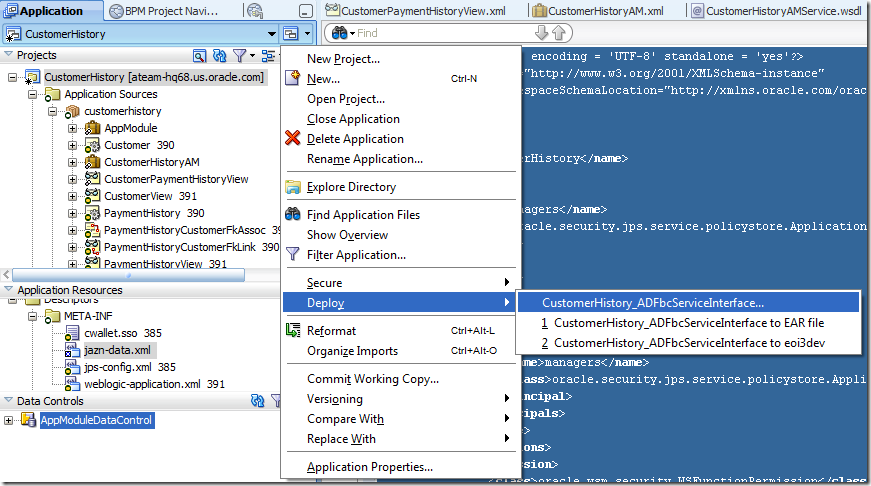
b) Now, to actually package the application into an EAR file, click the little screen sign next to the application name in JDev’s application navigator, as shown below.
Then pick the deployment profile you have just created and deploy it to an EAR file.
That’s it. Your secured service-enabled ADF BC is ready to de deployed.
Hope this is useful for you. Good luck!
Saturday, November 27, 2010
No Shortcuts To the Top
Just finished reading No Shortcuts to the Top: Climbing the World's 14 Highest Peaks. Extraordinary mountaineer Ed Viesturs describes his fascinating adventures across the highest mountains on Earth. He tells how he got to the top of the 14 peaks higher than 8000 meters without bottled oxygen. All about passion, being prepared, experience, taking the calculated risk and safety. Thumbs up!
Monday, October 25, 2010
Quick tip: OVD – Providing namespace translation for DN attributes
Breaking off the ADF/OPSS series…
OVD (Oracle Virtual Directory) guru Mark Wilcox gave me this really helpful tip that it’s worth sharing. It can save you folks quite a bit of headache.
Scenario: you have configured an OVD authentication provider in WLS, but you cannot login with any user from OVD in WLS Console, even the user being a member of an Administrators group in the backend LDAP directory. When you try it, you end up with an “Authentication Denied” error. And if you login into WLS Console in the “normal” way (i.e., using weblogic user from Default Authenticator provider) you don’t see the OVD users memberships. These two problems are definitely related.
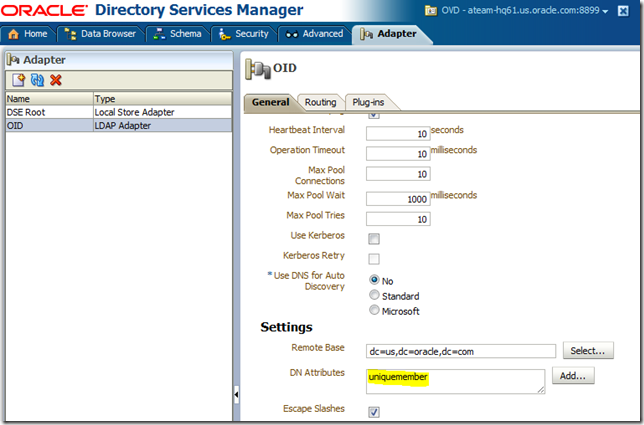
Solution: you need to change the LDAP adapter definition in OVD a bit. Connect to ODSM (Oracle Directory Services Manager), retrieve your adapter, click on the General tab and add uniquemeber as one of DN Attributes, as shown:
OVD translates all attributes listed as DN Attributes. Translation here means converting the backend repository (in this case OID) namespace into the adapter’s namespace. In this example, OID namespace is dc=us,dc=oracle,dc=com, while adapter’s is ou=oid,dc=us,dc=oracle,dc=com. Without the translation, uniquemembers of a group would end up being cn=<user>,dc=us,dc=oracle,dc=com. With the translation, they align nicely with the adapter’s namespace: cn=<user>,ou=oid,dc=us,dc=oracle,dc=com.
No need to restart anything. You should now be able to see users memberships as well as login in WLS Console with administrators users defined in the OVD authentication provider.
Note: this has been done in Oracle Identity Management 11g PS2.
Wednesday, October 20, 2010
Several ADF apps to one single OPSS policy stripe
In OPSS Artifacts Life Cycle in ADF Applications, I’ve explained how to change the default behavior for migration of authorization policies when deploying applications. Revisiting it, I’ve said that one can specify the MERGE value for jps.policystore.migration param-name in weblogic-application.xml and that is particularly useful in some deployments where more than one application have to share the same policy context (or policy stripe).
A real use case is when a customer wants to hide the concept of how a system is partitioned across ADF applications for security administrators. Most of the times, a security administrator is interested in the policies of the system as whole. This article explains how it can be done.
Before going further, some definitions:
- Policy Store: repository of policies comprising one or more application policy stripes and code-based grants. There’s only one policy store per WLS domain.
- Policy Stripe: set of application policies to which one or more applications bind to. One application binds to only one policy stripe.
Clarifying a little bit more, take the following system-jazn-data.xml snippet, the OOTB policy store in WLS domains. In such case, system-jazn-data.xml itself represents the policy store, while OrderEntry#V2.0 and OrderCapture#V2.0 are the policy stripes, defining an application-level scope for authorization policies. In default mode, OrderEntry application does not have access to application policies in OrderCapture#V2.0 policy stripe, and vice-versa.
<?xml version='1.0' encoding='utf-8'?>
<jazn-data>
<policy-store>
<applications>
<application>
<name>OrderEntry#V2.0</name>
<app-roles>
...
</app-roles>
<jazn-policy>
...
</jazn-policy>
</application>
<application>
<name>OrderCapture#V2.0</name>
<app-roles>
...
</app-roles>
<jazn-policy>
...
</jazn-policy>
</application>
</applications>
</policy-store>
</jazn-data>
When we develop an ADF application in JDeveloper and enables ADF security, the authorization policies you create go into a workspace-level jazn-data.xml under a stripe name that has the same name as the application itself, as show below. Let’s say our application is called OrderEntry. In jazn-data, we would have:
<?xml version='1.0' encoding='utf-8'?>
<jazn-data>
<policy-store>
<applications>
<application>
<name>OrderEntry</name>
<app-roles>
...
</app-roles>
<jazn-policy>
...
</jazn-policy>
</application>
</applications>
</policy-store>
</jazn-data>
Then if you do nothing and just deploy the application, the policies get migrated to the runtime policy store under an application policy stripe named OrderEntry#V2.0. For our mental sanity, the V2.0 comes from the Weblogic-Application-Version property in the MANIFEST.MF, but this is not the topic of this article.
Now what happens if we want to have OrderEntry and OrderCapture binding to the same policy stripe, say OrderMgmt? We need to add some properties to some deployment descriptors:
1) in weblogic-application.xml:
<application-param>
<param-name>jps.policystore.applicationid</param-name>
<param-value>OrderMgmt</param-value>
</application-param>
Such information is used only at deployment time. It basically tell the OPSS listeners to migrate application policies in jazn-data.xml to OrderMgmt policy stripe in the runtime policy store. In this scenario, the version number is not appended to the stripe name.
2) in web application’s web.xml:
<filter>
<filter-name>JpsFilter</filter-name>
<filter-class>oracle.security.jps.ee.http.JpsFilter</filter-class>
<init-param>
<param-name>enable.anonymous</param-name>
<param-value>true</param-value>
</init-param>
<init-param>
<param-name>remove.anonymous.role</param-name>
<param-value>false</param-value>
</init-param>
<init-param>
<param-name>application.name</param-name>
<param-value>OrderMgmt</param-value>
</init-param>
</filter>
Here I have added the init-param application.name to the JpsFilter definition. The param-value must match the value defined in weblogic-application.xml. This information is used only at runtime. It tells the JpsFilter where to bind to when looking for authorization policies. As the JpsFilter intercepts all requests for the Faces Servlet (javax.faces.webapp.FacesServlet), it establishes the policy store context for every request to an ADF artifact.
By repeating this very same configuration across your applications, you can bind any number of applications to the same policy stripe, i.e., the same authorization context and expose a single and consolidated view of your authorization policies to security administrators.
Monday, September 27, 2010
OPSS Artifacts Life Cycle in ADF applications
After writing about users and groups migration, it looked to me we should also talk about the life cycle of other important entities in secured ADF applications. When you enable security in an ADF application, you see a couple of new artifacts in your JDeveloper workspace, namely jps-config.xml, jazn-data.xml and cwallet.sso.
Have you ever wondered what their purpose is, their life cycle and how they relate to WLS domain security configuration? This article is just about it.
As you might know, secured ADF applications leverage OPSS (Oracle Platform Security Services).
OPSS is a fundamental component within Oracle Fusion Middleware security. It works as an abstraction layer on top of security services providers, shielding applications from all the complexities in dealing with them. For instance, applications can transparently switch between file-based and LDAP-based policy stores. Likewise for credential store services.
Let's take a closer look at each of those artifacts and their life cycles.
jps-config.xml
This file can be seen as the lookup services registry for OPSS. Among these services are login modules, authentication providers, authorization policy providers, credential stores and auditing services.
Whenever an OPSS-enabled application requires security services, it looks up a JPSContext object where all the necessary services are supposedly configured.
In ADF applications, a workspace-level jps-config.xml is created once ADF security is enabled. It drives services lookup for ADF's BC (Business Components) Tester available in JDeveloper, which is a JavaSE application.
If you want to have security unit tests, you can also easily leverage it.
It is never used once the ADF application gets deployed in a WLS container, even though it is packaged in the ear file. Within a WLS container, a jps-config.xml in <domain-home>/config/fmwconfig is used by all applications in all servers deployed in that WLS domain. There's no such concept of an application-level or server-level jps-config.xml.
jazn-data.xml
This file keeps users, groups and authorization policies for OPSS-enabled applications and is automatically created once ADF security is enabled. I've already covered users and groups life cycles in a previous article. It is important to mention that users and groups are also leveraged by ADF's BC Tester and can be integrated into security unit tests as well.
Authorization policies are, if not the most, one of the most sensitive parts of a secured ADF application, since it governs who has access to what. As you might guess, they are also leveraged by ADF's BC Tester. When the ADF application is deployed into WLS, at startup time, policies are OOTB (Out-Of-The-Box) migrated into the configured policy store, who, by default, is a file called system-jazn-data.xml, located under <domain-home>/config/fmwconfig. You can configure how (and if) policies are migrated through some properties in weblogic-application.xml. Here they are:
<listener>
<listener-class>oracle.security.jps.wls.listeners.JpsApplicationLifecycleListener<listener-class>
<listener>
This listener is the one actually responsible for pushing the changes to the runtime policy store. Make sure it is present in weblogic-application.xml. Otherwise, you’ll experience a lot of frustration in trying to deploy authorization policies along with your application.
<application-param>
<param-name>jps.policystore.migration</param-name>
<param-value>[MERGE|OVERWRITE|OFF]</param-value>
</application-param>
MERGE, OVERWRITE and OFF are exclusive and applicable for deployments and redeployments. And they mean exactly what you might be thinking.
- MERGE will merge what’s already available in the runtime policy store. This might be particularly useful in some advanced deployments where more than one application share the same application policy stripe.
- OVERWRITE wipes away the existing application policy stripe and load all policies from scratch.
- OFF skips policy migration.
Do notice that once the application is undeployed, its policies are also removed from the policy store, unless you set the following property in weblogic-application.xml:
<application-param>
<param-name>jps.policystore.removal</param-name>
<param-value>OFF</param-value>
</application-param>
Authorization policies migration will always happen according to weblogic-application.xml configuration, no matter what the deployment method is.
cwallet.sso
This file keeps credentials used by the application. A subtle and fundamental distinction is important to be made here: credentials and identities are not the same thing. Simply put, in OPSS, identities are what authentication requests are done against, while credentials are securely kept objects that are somehow presented to authentication providers to be matched against identities.
cwallet.sso is encrypted and you cannot browse it or explicitly edit it via JDeveloper. At design-time, different components make use of cwallet.sso and are responsible for creating the necessary credentials in it. Examples are OWSM policy attachments that override the csf-key and ADF connections requiring credentials in the call out.
If you need credentials that can’t be created within JDeveloper, you can either use wlst createCred online command or write some code using OPSS APIs. Both options makes the whole life cycle story a little catchy, because a running WLS container is necessary. You can also disable credentials migration and create them directly in the WLS domain where applications are deployed.
Like authorization policies, credentials are also OOTB migrated into the configured WLS domain credential store on application startup. By default, the credential store is the cwallet.sso file in <domain-home>/config/fmwconfig folder.
The following weblogic-application.xml properties govern how (and if) they're deployed.
<listener>
<listener-class>oracle.security.jps.wls.listeners.JpsApplicationLifecycleListener</listener-class>
</listener>
As for policies, the same listener migrates credentials. Avoid frustration and make sure the listener is present if you want to migrate or control how your credentials are migrated.
<application-param>
<param-name>jps.credstore.migration</param-name>
<param-value>[MERGE|OVERWRITE|OFF]</param-value>
</application-param>
- MERGE: migrate non-existing credentials only;
- OVERWRITE: overwrites existing credentials;
- OFF: skips credentials migration;